Modern software heavily depends on a multitude of libraries (often several hundreds even for small projects), and the Apache Log4j incident serves as a stark reminder that even a single software vulnerability within an apparent harmless library can potentially compromise the entire system and serve as an entry point for attacks on interconnected IT systems.
When the Log4j threat became known, how did your company respond? Did you find yourself in a situation where you had to contact Paul, dial Lina’s number, correspond with your IT solution provider, and, despite these efforts, you remained without a precise response for several hours?

How not to sink ?
Our solution Dependency Track SaaS keeps a meticulous record of all software components and their dependencies, spanning not just one layer but every chain of dependencies. For each software, you get a comprehensive breakdown of the complete chain of components, including their version numbers and license types.
With our solution, you can not only answer questions like, “Is software XYZ using Log4j?” but you can also directly answer the question “Which of my software applications still employ directly or not a vulnerable versions of Log4j?”
Learn to surf like a pro effortlessly
We understand that sometimes you might not even be aware that Log4j should be on your radar. Dependency Track SaaS scanner operates continuously, monitoring all dependencies and promptly alerting you to any known software vulnerabilities within your components. Furthermore, our intuitive dashboards offer a bird’s-eye view of threats, aiding you in strategizing your software updates.
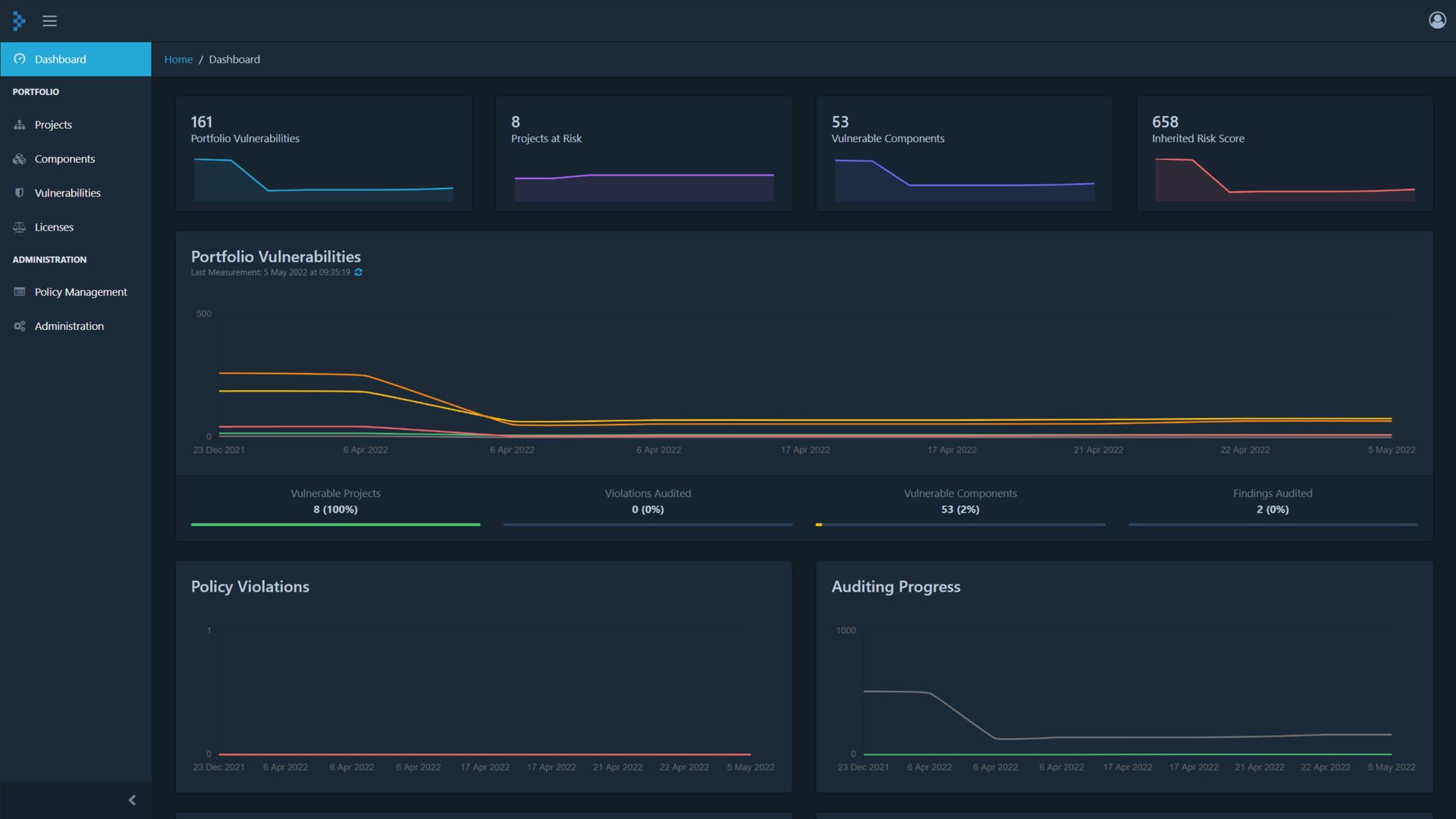
So, the next time your boss inquires, you can confidently affirm that you’ve taken proactive measures, and all affected software components have been identified.
Regain control now
Contact us